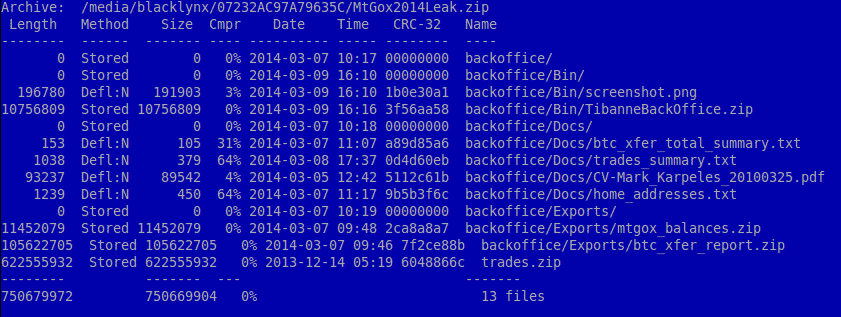
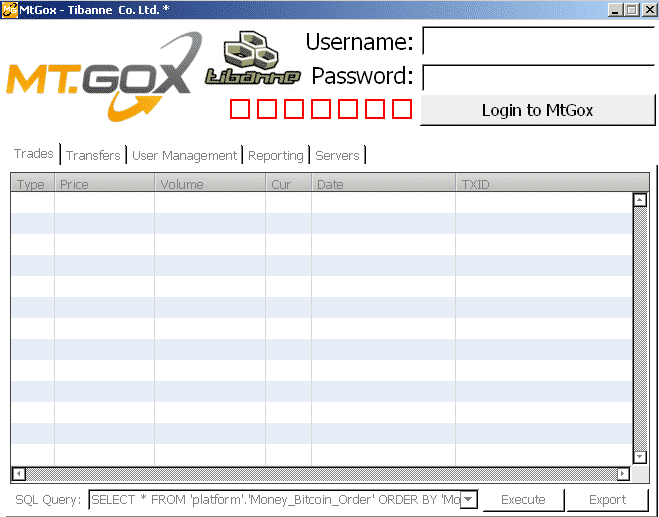
The file when executed creates and executes the TibanneSocket.exe binary and searches for the files bitcoin.conf and wallet.dat and sends it to remotely located command and control server. Kaspersky have managed to locate of the C & C server and found it to be in Bulgaria. The server was offline at the time of writing of this article. Since most people are curious to see the leaked data, the trojan creator smelled a opportunity and released the malicious code through the binaries. It was reported by Kaspersky that the creator was actually successful in spreading the malware though it could not be ascertained whether the attacker managed to remotely access any of the victims bitcoin wallets.Indepth Analysis of the Malware can be seen from the Securelist blog